Are You Ready to Witness the Future of Data Security?
Platform
©2026 QuNu Labs Private Limited, All Rights Reserved.

Your encrypted data is already being stolen. Not hacked—stolen. Stored on servers somewhere, waiting.
This is the "harvest now, decrypt later" dilemma, and it's not hypothetical. Adversaries are capturing encrypted data today with the expectation that the advent of quantum computers in the decade ahead will render the currently unbreakable, breakable. With the advent of a sufficiently capable quantum computer, today's RSA-2048 encryption—which is the standard for protecting everything we do from bank transfers to state secrets—would be broken within hours, not in millennia. Singapore is not waiting to see what happens next.ens next.
Singapore has committed over S$400 million through 2030 to quantum technology, with a clear focus on security. The National Quantum Strategy allocated nearly S$300 million from the Research, Innovation, and Enterprise 2025 plan. The Monetary Authority of Singapore added S$100 million specifically for financial sector quantum capabilities. In March 2025, another $24.5 million went to the Hybrid Quantum Classical Computing initiative.
But here's what separates Singapore from other quantum initiatives: the money isn't going to research papers. It's funding production deployments.
DBS, HSBC, OCBC, and UOB just finished testing quantum key distribution in a Monetary Authority of Singapore sandbox that ran from September 2024 to March 2025. Singtel launched Southeast Asia's first nationwide quantum-safe network in August 2024, and enterprises are already using it. The Ministry of Defence is building a Quantum Sensing Centre for GPS-denied navigation. This isn't innovation theatre. It's infrastructure.
The cryptographic algorithms securing today's digital world—RSA, Elliptic Curve Cryptography—rely on mathematical problems that classical computers can't solve in any reasonable timeframe. A quantum computer changes that calculation entirely. What would take a supercomputer thousands of years could take a quantum computer hours.
The Monetary Authority of Singapore states this plainly - “quantum computers threaten the cryptographic algorithms securing financial transactions, customer data, and interbank communications.”
But the threat isn't just about when quantum computers arrive. Medical records encrypted today need to stay confidential for decades. Financial documents have long-term sensitivity. Defence communications can't be compromised years after the fact. If that data is stolen now and stored, it becomes vulnerable the moment quantum computers become powerful enough.
Singapore's 730 square kilometres make it the ideal testing ground for quantum security infrastructure. What works across Singapore can scale regionally. ASEAN markets are watching. When Singapore proves quantum security is practical, affordable, and accessible as a service, neighbouring countries have a blueprint to follow.
The Digital Connectivity Blueprint outlines this journey: “research funding leads to startup creation, startups build technology, enterprises test it in sandboxes, regulators create frameworks, and infrastructure providers make it accessible as a service. Each step validates the next.”
IMDA is co-leading efforts with Japan to establish a QKD protocol framework at the International Telecommunication Union. Singapore is working towards integration with quantum-ready networks from like-minded countries, allowing enterprises to deploy quantum-safe solutions across global markets. This isn't just national infrastructure. It's the foundation for regional and international quantum-safe communications.
Between September 2024 and March 2025, MAS ran a proof-of-concept sandbox that moved beyond demos. Banks deployed Quantum Key Distribution stacks to encrypt settlement files between themselves and MAS, measuring real operational metrics under production-like conditions.
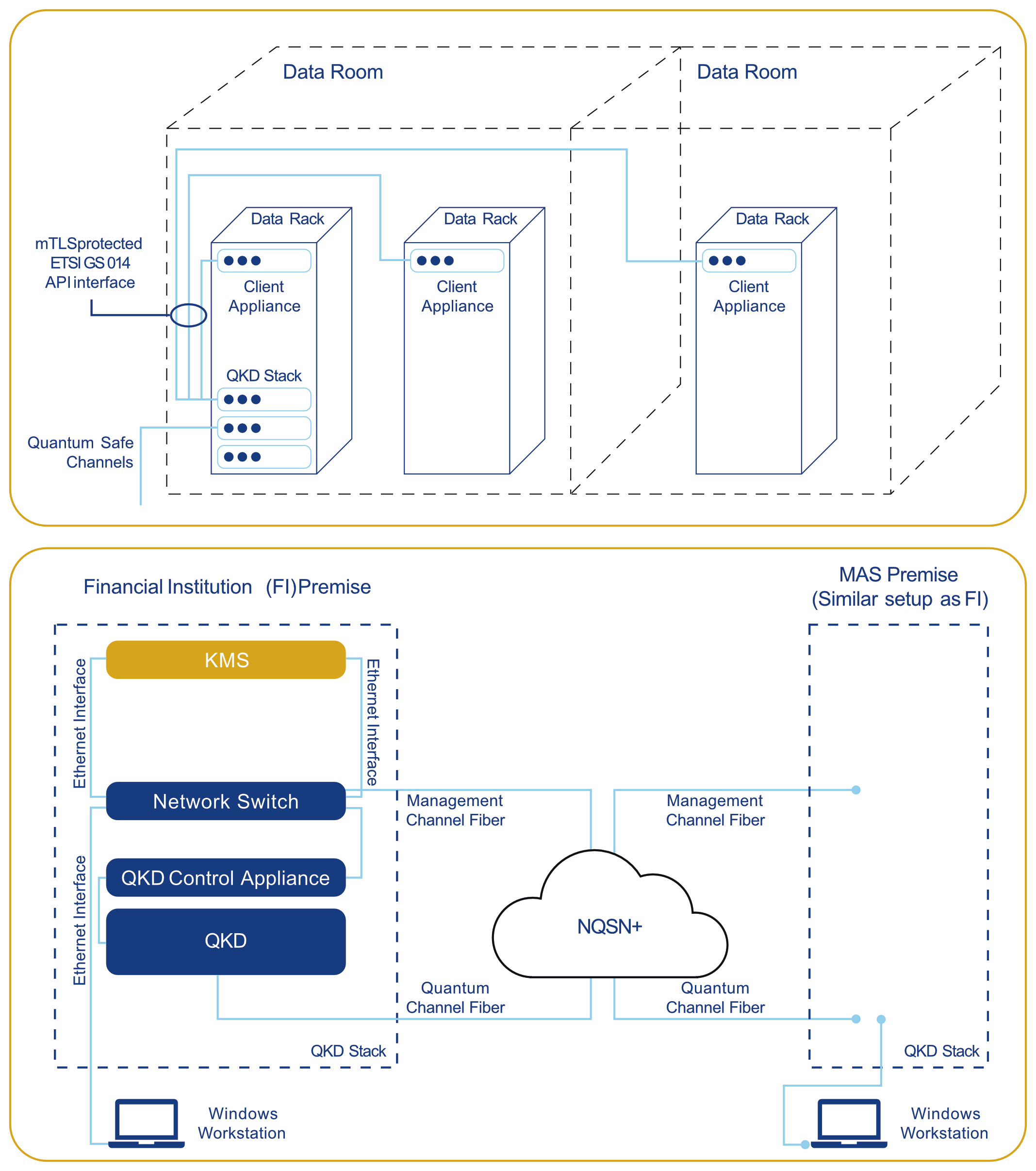
The system generated 6.75 million AES-256 keys per day per bank. The buffer capacity? Enough for 2.5 months of encrypted operations during network outages or equipment failures. Banks simulated eavesdropping attacks and fibre disconnections, measuring Secure Key Rate and Quantum Bit Error Rate throughout.
The takeaway wasn't that quantum key distribution is perfect. It was that QKD can integrate with existing infrastructure without complete network overhauls. The keys generated through quantum physics provide security beyond algorithmic resistance—if someone intercepts the keys, the quantum state collapses and the interception is detected. That's fundamentally different from classical encryption, where an attacker can copy encrypted data without leaving any trace.
OCBC is now running a year-long research collaboration with NUS, NTU, and SMU exploring quantum algorithms for derivative pricing and fraud detection. What currently takes hours in Monte Carlo simulations could potentially run in minutes. Pattern recognition for transaction anomalies gets a computational boost from quantum machine learning.
The Ministry of Defence's Quantum Sensing Centre addresses a different quantum problem: navigation when GPS fails.
GPS signals can be jammed, spoofed, or simply don't penetrate underwater or underground. Military operations need navigation that works everywhere. So do autonomous vehicles operating in urban environments and critical infrastructure in contested areas.
Quantum sensors use atom interferometry to measure acceleration and rotation with extraordinary precision. Unlike GPS, quantum inertial navigation is self-contained. A submarine navigates underwater for weeks. An autonomous vehicle operates in tunnels. Defence systems work in GPS-denied environments.
Singapore startups are commercialising exactly this technology—quantum sensors that work underwater, underground, and anywhere GPS can't reach.
Start-ups are investing in satellite-based quantum communication. The are working in an interoperable Optical Ground Station for satellite-based Quantum Key Distribution between Asia and Europe, with the first station planned for Singapore.
To date, close to $3 billion has been invested in over 330 startups. This is commercial investment expecting returns, not research grants.
At Singapore International Cyber Week 2025, the Cyber Security Agency of Singapore released a Quantum-Safe Handbook and Quantum Readiness Index. The handbook provides practical guidance for quantum-safe migration. The Quantum Readiness Index is a self-assessment helping organisations gauge readiness and prioritise actions.
Both documents are under public consultation through December 2025. This consultation process ensures final guidance reflects operational constraints, not just security ideals.
Professor Alexander Ling, principal investigator at Singapore's National Quantum-Safe Network, advises organisations to monitor trends and adopt standards endorsed by regulators.
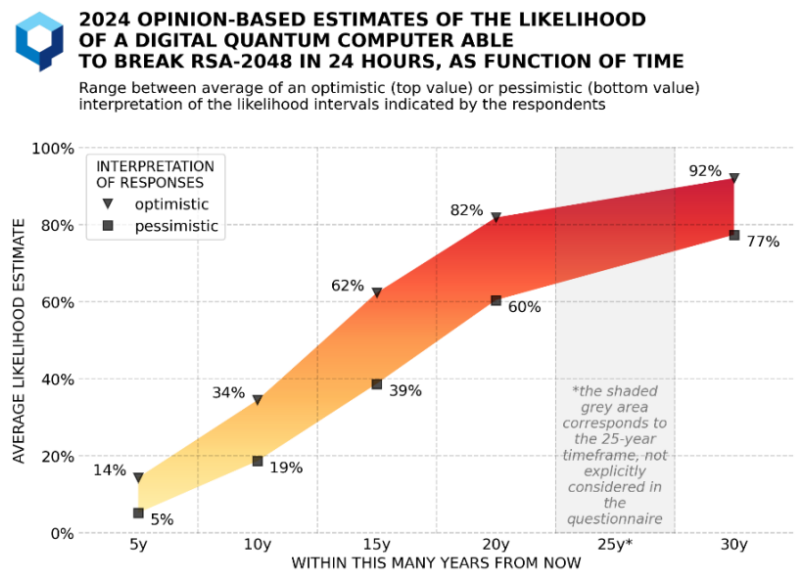
A July 2025 Capgemini Research Institute report found that nearly two-thirds of organisations consider quantum computing the most critical cybersecurity threat in 3-5 years. Six in ten early adopters predict Q-day—when quantum computers can break current encryption—within 5-10 years.
That timeline has compressed. Estimates a decade ago suggested 15-20 years. The consensus is now 5-10 years, with some researchers suggesting it could happen sooner.
The World Economic Forum estimates quantum computing could generate up to $622 billion in value by 2035 in financial services alone. That value accrues to organisations preparing infrastructure now, not those scrambling to retrofit quantum security whilst competitors are already running quantum-optimised algorithms.

For organisations exploring quantum-safe solutions, companies like QNu Labs offer integrated platforms covering quantum random number generators, quantum key distribution systems, and post-quantum cryptography working together. Learn about QNu Labs' approach to quantum security.
Your encrypted data is already at risk. Singapore's banks aren't testing quantum security for competitive advantage alone—they're preparing for regulatory requirements.
Early adopters gain expertise before crisis-mode deployment. They position themselves to use quantum computing's benefits whilst defending against its threats. Singapore's bet is clear: quantum security is infrastructure, not innovation.
The question isn't whether to prepare. It's whether you're leading or following.
Connect with QNu Labs to explore quantum-safe solutions for your industry.
Singtel's Quantum-Safe as a Service shifts costs from capital to operational expenditure. Instead of buying quantum hardware, enterprises subscribe to quantum-safe communications. This makes quantum security accessible to organisations of any size, not just enterprises with massive security budgets.
Singapore is pursuing both because they serve different purposes. Post-quantum cryptography (PQC) uses mathematical algorithms designed to resist quantum attacks. Quantum key distribution (QKD) uses quantum physics to detect if someone is intercepting cryptographic keys. The MAS sandbox tested QKD specifically because it provides security properties beyond algorithmic resistance—you know immediately if someone is attempting interception.
IBM estimates 12 years to fully adopt post-quantum cryptography. That's not 12 years of installation. It's 12 years of discovering where cryptography exists in your systems, testing quantum-safe alternatives without breaking existing applications, and migrating enterprise-wide. Waiting means attempting this migration while adversaries may already have quantum capabilities and your competitors have quantum-resistant infrastructure already in place.
Defence and banking are leading adoption because they handle data with the longest confidentiality requirements and the highest consequences for breach. Healthcare should follow immediately—patient data is permanent. Telecommunications and critical infrastructure operators need quantum security to protect the networks others depend on. Any industry handling data that must remain confidential for decades needs to act now.
Crypto-agility means your systems can rapidly adapt cryptographic mechanisms as threats evolve and standards change. New quantum-safe standards will continue emerging. Regulations will evolve. Vulnerabilities may be discovered in specific algorithms. Crypto-agile systems let you swap cryptographic components without rebuilding applications. It's the difference between changing tyres and rebuilding the entire vehicle.