Are You Ready to Witness the Future of Data Security?
Platform
©2026 QuNu Labs Private Limited, All Rights Reserved.
To lead as a thought leader in the quantum era, it is essential to align with strategic frameworks set by national bodies like CERT-In (Indian Computer Emergency Response Team). As the national nodal agency for cybersecurity under the Ministry of Electronics and Information Technology (MeitY), CERT-In’s guidelines designated under the Information Technology Amendment Act 2008, are the gold standards for Indian enterprise security.
Their recent whitepaper, "Transitioning to Quantum Cyber Readiness," is a call to action. It highlights that the quantum computing era is a present-day inflection point with far-reaching implications for digital infrastructure.
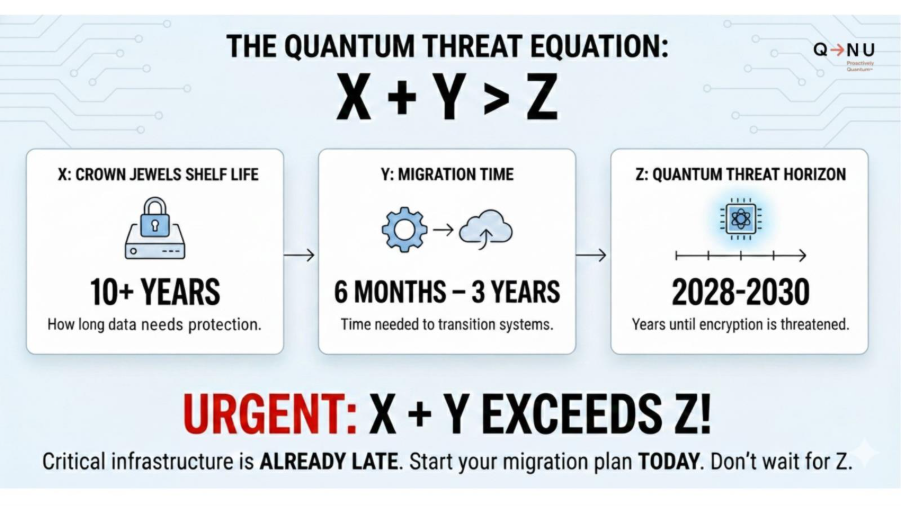
The urgency boils down to simple mathematics: X + Y > Z
If X + Y exceeds Z, you are already late. For most critical infrastructure organisations, the equation tilts dangerously towards urgent action. This is not just a theoretical finding; this is happening now.
Google's Willow chip achieved exponential error reduction with 105 qubits in December 2024. Microsoft's Majorana-1 processor, launching in February 2025, scales to one million qubits. The United Nation (UN) declared 2025 the International Year of Quantum Science and Technology. So, the quantum era is not approaching, rather it is already here.
McKinsey reports that the potential economic value of quantum technology will reach $2 trillion by 2035 across industries. However, this same power threatens the $173 billion global cybersecurity market. Gartner predicts that by 2029, 20% of organizations migrate to post-quantum cryptography (PQC), which is less than 1% today.
Nation-states and sophisticated actors are already harvesting encrypted data today, storing it until quantum computers can break current cryptographic systems. USA, EU, India, Singapore, Japan, UK, Australia, GCCs have acknowledged this as immediate threat.
Know more about Quantum Threat Assessment.
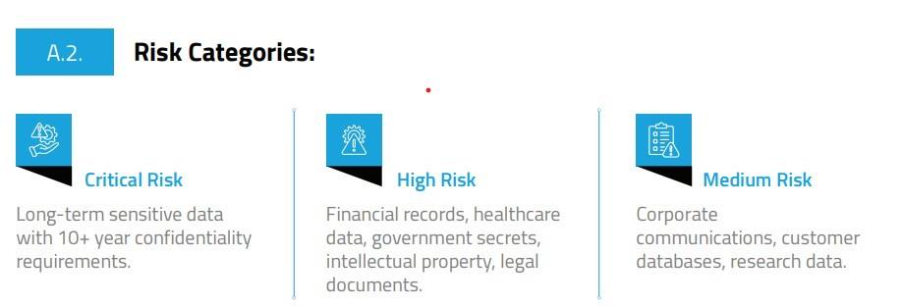
Any data requiring protection beyond 2030 should be considered at immediate risk: government secrets, intellectual property, medical records, financial instruments, legal documents.
The whitepaper outlines a structured approach to quantum-safe migration through four critical phases:
Visibility is the first line of defence. Organisations must identify where quantum-vulnerable cryptography (like RSA or ECC) resides.
Action: Take a quick ‘Quantum Risk Assessment’ to evaluate where you stand in terms of Quantum readiness
This phase focuses on adopting transitional strategies to bridge existing systems with emerging solutions.
Organisation requires a tiered timeline to migrate from traditional security toquantum security:
Also, check out this educational video – how to start with your PQC Migration or overall PQC Migration Journey

Finalize the transition by embedding long-term agility.
A major securities exchange in APAC handles billions in daily trading volumes. The challenge? Protecting high-frequency trading data without compromising the sub-millisecond latency that markets demand. QRNG was implemented for enhanced key generation and deployed hybrid PQC across their trading infrastructure.
There was zero downtime during migration, and trading speeds maintained with the help of QNu Labs. When your competition measures advantage in microseconds, this matters.
Imagine securing millions of daily transactions across an entire nation's retail payment network, UPI transfers, card payments, bank settlements, all whilst maintaining 99.99% uptime. We partnered with a national payment infrastructure provider to deploy hybrid cryptography across distributed payment gateways and establish continuous monitoring frameworks.
Twenty-four months later, 70% of critical infrastructure runs on quantum-safe protocols with zero transaction failures. That is not just security, it is national digital resilience.
The complexity of multi-tenant government data centre hosting sensitive information across various departments is not just technical; it had architectural challenges as well. QNu labs deployed PQC for tenant data encryption.
This resulted in quantum-ready certification for highest-security tenants and a replicable blueprint now being adopted nationwide. One successful deployment becomes a template for an entire nation.
One of the world's largest transport networks faced a unique challenge: protecting critical signalling infrastructure and passenger data across systems ranging from modern cloud platforms to decades-old, embedded controllers. Standard PQC implementations could not work on resource-constrained IoT devices managing railway signals.
QNu Labs developed a tailored hybrid approach specifically for these constraints, implementing quantum-safe firmware signing whilst maintaining 99.99% operational availability to safeguard data against quantum threat for millions of daily passengers who depend on this infrastructure.
At QNu Labs, we help Government, PSU, and Defence organisations navigate this transition using our proprietary process as mentioned below.
The quantum threat clock started ticking the moment your sensitive data was first stored using vulnerable encryption. Do not wait for the threat to arrive.
CERT-In's whitepaper "Transitioning to Quantum Cyber Readiness" is available at www.cert-in.org.in. QNu Labs is an independent quantum security solutions provider aligned with CERT-In's strategic framework.
It is a strategy where adversaries collect encrypted data today to decrypt it once they have a quantum computer. Read here to know more.
A formula (X+Y>Z) used to calculate urgency. If your data shelf-life (X) plus migration time (Y) is greater than the time until a quantum threat (Z), you are at risk.
It allows systems to switch cryptographic algorithms as easily as a software patch, avoiding costly hardware overhauls as threats evolve.
Typically, 6 months to 3 years depending on infrastructure complexity. However, high-risk systems should be prioritised for immediate protection within 3–6 months.
Yes. Hybrid cryptography layers quantum-resistant algorithms alongside existing classical cryptography, providing protection during transition without wholesale infrastructure replacement.
PQC refers to mathematical algorithms designed to be secure against attacks by both quantum and classical computers. Unlike current RSA or ECC, these are based on complex mathematical problems like lattices or codes that quantum computers cannot easily solve.
QKD is a hardware-based method that uses the principles of quantum mechanics to distribute secret keys. Any attempt to intercept the key changes its quantum state, immediately alerting the communicating parties. Know more about QKD here.
Costs vary based on the size of the ICT infrastructure and whether you are implementing software-based PQC or hardware-based QKD. However, starting with a Quantum Readiness Assessment or a QNu Starter Kit is a cost-effective way to begin.