Our products Armos(QKD) and Tropos(QRNG) are now on GeM's portal
Quantum computing uses fundamental principles of quantum mechanics to perform complex processing. Quantum cryptography leverages the same principles for advanced data encryption. However, quantum computing and quantum cryptography are not allies. Instead, they stand tall against each other at the crossroads!
Ironical as it may sound, quantum cryptography was born because of the fear of quantum computing breaking existing encryption protocols. A quantum computer of a scale of about 1000 qubits can break RSA codes that protect online data exchange today in seconds. When the entire security infrastructure we have known for decades can collapse in the blink of an eye, the collateral damage is too high to ignore.
Symmetric vs asymmetric encryption
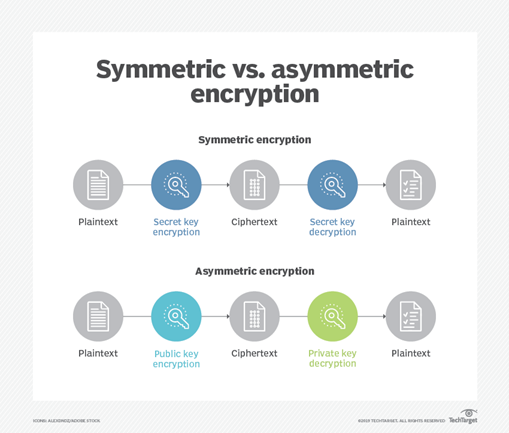
Most organisations deploy symmetric or asymmetric encryption to protect their assets such as data storage devices, networking devices, secure email, and web browsing. Symmetric algorithms are easier to break than asymmetric algorithms. Therefore, RSA encryption and most other public key cryptographies are asymmetric. Complex mathematical structures that use large prime numbers were the bedrock of asymmetric encryption because classical computers took thousands of years to crack the code.
Quantum Computing - A Game Changer
With the advent of quantum computing, the scenarios have changed completely. A quantum computer can break asymmetric algorithms in seconds posing a threat to security infrastructure. Malicious actors aka cybercriminals are harvesting data now so that they can decrypt it later and hold companies at ransom. The activity is so widespread that it has a term for it – Harvest Now Decrypt Later (HNDL).
Possible Alternatives Under Quantum Cryptography
Many quantum-resistant alternatives are available that are collectively termed quantum cryptography. However, quantum key distribution (QKD), quantum random number generator (QRNG), and post-quantum cryptography (PQC) are globally accepted as the most robust technologies among them.
QKD works on the quantum principle of entanglement. The two quantum particles are correlated such that the state of one particle affects the state of the other particle, even when they are separated by a large distance. Any attempt to intercept or measure particles during the transmission would disturb their state, and the disturbance would be detected by Alice and Bob, alerting them to the presence of an eavesdropper.
Quantum random number generators (QRNGs) generate randomness using quantum principles, which are non-deterministic. QRNGs offer multiple advantages: quantum indeterminacy, faster performances by leveraging photonics, and the ability to verify the origin of unpredictability.
According to NIST, lattice-based algorithms were robust for PQC. The algorithms are designed for two main tasks for which encryption is typically used: general encryption, used to protect information exchanged across a public network; and digital signatures, used for identity authentication. For general encryption, used to access secure websites, NIST selected the CRYSTALS-Kyber algorithm. The advantages are comparatively small encryption keys that two parties can exchange easily, as well as the speed of operation. For digital signatures, often used to verify identities during a digital transaction or to sign a document remotely, NIST selected three algorithms. Three of the selected algorithms are based on a family of maths problems called structured lattices, and one uses a hash function.
How can QNu Labs Help?
QNu Labs is a pioneer in developing products that proactively secure data for the post-quantum era.
QNu’s range of quantum-based products covers security from end-to-end across the entire data-based paraphernalia. From quantum-based encryptions to entropy enhancement services, QNu covers all security bases.
QNu’s flagship products Armos (QKD), Tropos (QRNG), and Hodos (PQC) are a perfect start to your quantum-cryptography journey of protecting your data.
It is time to use quantum cryptography against quantum-powered attacks.
