Why Quantum Cryptography Requires Policy Mandates from the Authorities
JUNE 06, 2024 | QNu Labs
SHARE
Quantum cryptography offers a significant leap in security for critical industries that rely on creating, processing, and storing digital data that are of national importance.
Industries such as banking, healthcare, power grids, and telecom (critical digital infrastructure) are at risk as quantum computers become more powerful, and the potential for systems compromise in these industries continues to grow with every passing day.
Here are some important use cases for these industries that warrant immediate attention and action by the various regulatory bodies governing them:
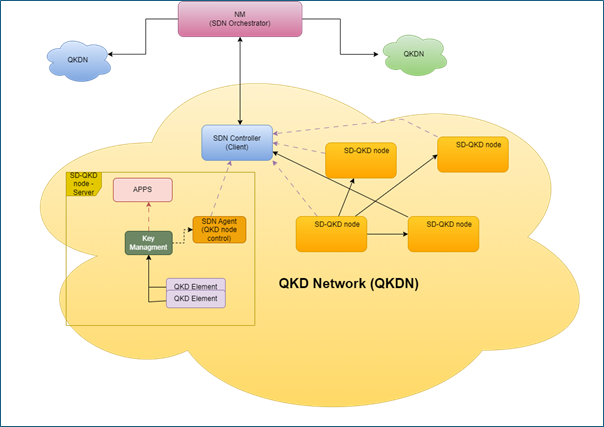
- Securing sensitive communication: Traditional encryption methods used today are vulnerable to hacks by future quantum computers. Quantum Key Distribution (QKD) uses the principles of quantum mechanics to create unbreakable keys for secure communication of sensitive data like financial transactions, account details, healthcare records, last-mile connectivity in telecom networks, and grid control information systems.
- Protecting against “harvest now, decrypt later” attacks: Hackers can steal encrypted data today and wait for quantum computers to evolve. Once powerful quantum computers are available, they could decrypt the earlier stolen data, giving them access to past transactions in banking and compromising financial security. Similar risks exist in healthcare (a recent example is AIMS attack), and telecom and power grid infra that could result in countrywide chaos. Quantum cryptography, especially QKD eliminates these risks by making the cryptographic key uncrackable.
- Securing online digital economy: banking and inter-bank payment systems: Quantum cryptography can safeguard online banking sessions and digital payment transaction systems, e-health record storage and exchange, and data of electrical and telecom grid networks, by providing a secure mechanism to generate robust quantum keys and a secured channel for exchanging encryption keys. It ensures that only authorized parties can access and modify digital data.
- Generating random numbers for cryptography: Quantum Random Number Generators (QRNGs) exploit quantum phenomena to create truly random numbers, a crucial element in strong encryption. Critical industries of national importance can leverage QRNGs to generate unpredictable keys and strengthen their overall cryptographic defenses. They fortress tokenization systems, PII data safeguarding, data vaults, API salts, one-time passwords (OTPs), and other business-critical applications. By implementing quantum cryptography, these industries can ensure the confidentiality and integrity of financial data in the quantum computing era.
Implementing the quantum technologies mentioned above requires policy changes. The crucial government departments should take action to prioritise security in every organisation.
For instance, RBI must introduce the adoption of quantum cryptography into the Indian Banking Cybersecurity Framework, DoT should mandate using quantum cryptography for telecom networks, the Ministry of Power must release guidance mandating power entities to migrate to quantum cryptography and the Regulation for Digital Healthcare should embrace quantum cryptography at its core.
Without adequate government support and stringent policy guidelines, quantum cryptography might not realise its true potential in India’s cybersecurity ecosystem.