Guide: QOSMOS - Entropy as a Service and How it Works
The guide details the concept of EaaS, its methodology, and industry applications.

Table of Contents
The Context
Every device, especially in the hyper-connected world of today, ought to communicate securely on the internet to minimise data exposure risks. Cryptography plays a critical role in ensuring the data remains secure when idle or in transit.However, cryptography fails when devices work with weak random numbers generated from low-entropy sources and use predictable keys.
The best source of true randomness is from unpredictable physical phenomena of quantum effects. Leveraging it in individual devices is impractical because of their various limitations - form factor, hardware age, power consumption, and interface availability. To enable organisations to overcome these hurdles, QNu Labs created “QOSMOS”, a quantum-secure EaaS (Entropy as a Service), that helps organisations, developers, and security teams to get access to quantum-sourced random numbers for use with any application for cryptographic key generation.
What is Entropy as a Service?
In computing, entropy is the randomness collected by a system used in any application that requires random data. It forms the basis of cryptography in cybersecurity.
The security of a system depends on the secrecy of the keys, which should be impossible to crack. This is why randomness is important. The randomness comes from either pre-existing hardware resources or specially provided randomness generators. Entropy is a constant stream of very high-quality random numbers, which can be fused with the entropy already collected by your computer.
EaaS is a security service architecture that provides secure time and quantum entropy sources for multiple devices including IoT.
The standard deterministic computers cannot deliver appropriate randomness, especially for devices with little opportunity to build entropy locally. The best sources of true randomness are based on unpredictable physical phenomena, such as quantum effects.
QOSMOS (Entropy as a Service) solves the entropy starvation problem of systems, whether in a cloud, embedded systems, or at the edge.
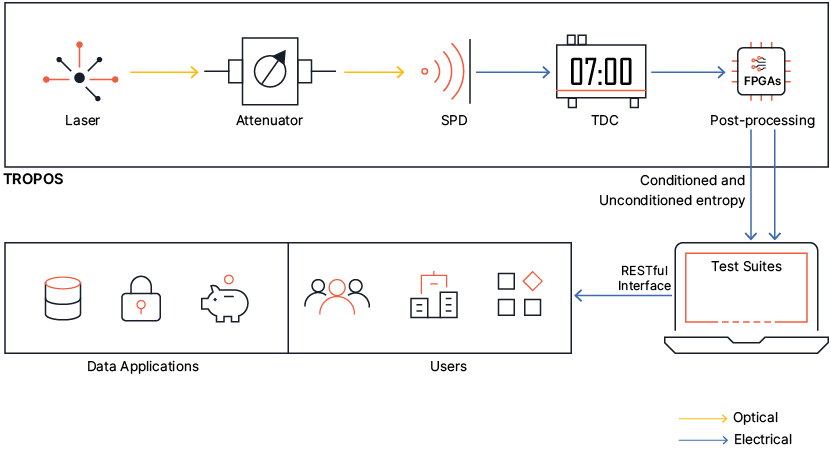
The Architecture of QOSMOS

The architecture comprises three main sections:
- TROPOS (QRNG) QNu’s flagship product, Tropos, is a quantum entropy device that is the root of randomness. The random numbers are generated from a quantum source and then transferred to applications as a service through QOSMOS architecture. Tropos generates a continuous stream of random bits fed to the EaaS Server.
- EaaS (Entropy as a Service) Server The EaaS server acts as a bridge between Tropos and the client application. The EaaS server accesses the random number stream (QRNG) which is signed, encrypted, and sent along with the timestamp to the client application. The USA-based NIST suggests accessing multiple EaaS servers to increase seed security, and the EaaS server architecture is scalable and can span servers worldwide.
- Client HRT or Application HRT (Hardware Root of Trust) is a classical computing device with secure hardware components for storing, seeding, and generating cryptographic keys. HRT would be TPM, Intel IPT, ARM TrustZone, HSM, or any encryption key generation device. It can also be combined with a client software application which enables communication between the EaaS server and client hardware. It is not required for the client system to have dedicated hardware, but the hardware availability will make the process more secure.
Characteristics of QOSMOS
- Lack of pattern: QOSMOS provides truly random numbers with a steady supply of information that cannot be predicted or exploited by hackers.
- Proactive quantum entropy: Quantum sources power the entropy generated by QOSMOS. Clients can rest be assured that the system cannot be attacked to degrade the entropy.
- Ease of Integration: API runtime provides a seamless integration i.e., a new module or feature of an application or hardware can be added or integrated without resulting in any errors or complications.
- Multiple deployments: The solution can be hosted in the client data centre or the cloud. By hosting QOSMOS in their data centre, clients can benefit from extra security.
- High Scalability:QOSMOS is designed from the ground up to be highly scalable. It is powered by multiple quantum sources to ensure redundancy. Even if one of the quantum sources fails, clients are still assured of high quantum entropy from other connected devices.
- Minimum Latency: Dynamic load balancer ensures that the least occupied device will cater to requests. This ensures the system will not suffer latencies when receiving random numbers from QOSMOS.
- Proof of Randomness: The random data is subjected to a battery of tests specified by standards like NIST/ENT and only after successful verification, the buffers are served. The client also has the option to download the reports offline and verify.
Applications of QOSMOS
The use cases for QOSMOS are wide and diverse. Some of the immediate applications are:
- Web browser security
- Encrypted email
- Secure video conferencing
- Secure video conferencing
- Data backup & recovery
- Remote monitoring & management software
- Digital signatures
QOSMOS (EaaS) provides the highest quality randomness and a secure method of providing the seeds for entropy-starved systems or applications.