How should security teams prepare for post quantum cryptography?
The post-quantum world poses a threat to the existing cybersecurity systems.
Quantum computers use the laws of quantum mechanics to process information in quantum bits or qubits. Qubits can exist in multiple states at the same time (called quantum superposition). This property allows quantum computers to process data and solve problems exponentially faster than classical computers. It has been proven that a scaled quantum computer will render modern public-key encryption algorithms useless. Many enterprise technologies depend on public-key encryption, placing them at an elevated risk of brute-force attacks by malicious actors.
The power of quantum computing can easily break RSA protocols that guard our online data. RSA-2048, once considered a fortress of cybersecurity, is vulnerable to quantum hacks. It has become imperative for organisations to protect sensitive and critical data with quantum-resistant cryptography.
Migration to Quantum-Safe Encryption (QSE)
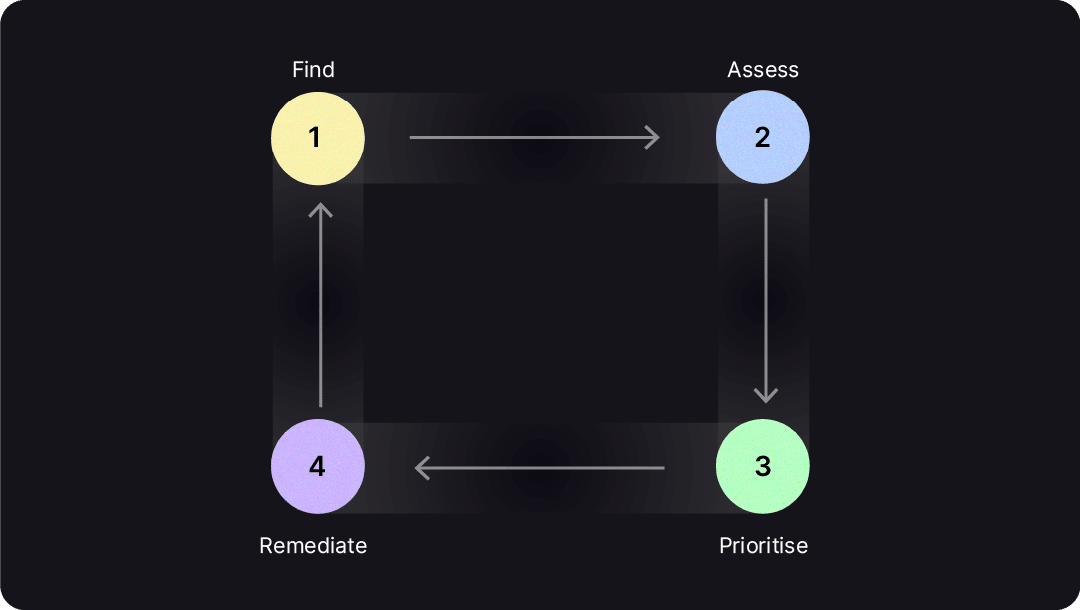
The migration from existing encryption towards quantum cryptography can be a challenging endeavour. It requires the participation of people, processes, and technology. Quantum cryptography is an evolving technology that will go through a series of iterations with time. Transitioning to QSE, as of today, can be explained in four steps:
Find:
The first step is to collect the inventory of cryptographic assets used by the organisation. It includes algorithms, keys, certificates, protocols, and libraries. It typically consists of a scanner capable of scanning an application, a host, or a network and an inventory of cryptographic assets.
Assess:
The second step is to look for vulnerabilities across the collected cryptographic inventory. The need to transition to QSE provides an excellent opportunity to modernise encryption implementation overall. Therefore, the vulnerabilities should not be limited to finding algorithms that are not quantum-safe. They can include any cryptographic vulnerabilities.
Prioritise:
The third step is prioritising the vulnerabilities discovered based on risk so that the organisation addresses the highest risks first. This risk-based prioritisation requires enrichment data.
Let’s consider two databases that we need to rank for priority. Suppose that database A contains classified information while database B contains public information. The data classification information is an example of enrichment data. This context prioritises fixing the issue for database A, which poses a higher risk.
Remediate:
This step automates the remediation of those prioritised issues. The remediation procedure differs depending on whether the issue requires an application change. For issues that do not require an application change, this step integrates with external systems to drive a resolution.
Roadmap for security teams in an organisation
The migration to quantum-safe algorithms could take several years, for some industries like healthcare and financial services, the transition can be challenging due to technology lifecycles and long-life data that has to remain secure. The transition to post-quantum is considered more complex than previous cryptographic transitions. It should serve as a wake-up call for considering the impacts on a company's digital infrastructure.
To kick-start the migration, the security teams need to:
Inventory data: Map out where the most sensitive and long-life data resides.
Inventory cryptographic assets: Gain in-depth visibility into what cryptographic assets already exist in the technology environment.
Build a cryptographic agility strategy: Cryptographic agility is the ability to easily move from one algorithm to another – even a quantum-resistant one.
Test and plan the migration: Follow steps 3 and 4 mentioned earlier for seamless migration.
Overview of post quantum cryptography solutions The adjustments and investments security leaders will need to make depend on the type of post quantum cryptography solution.
The two most viable candidates are:
In quantum key distribution (QKD), two parties exchange a symmetric key through a secure quantum channel. This solution requires additional quantum hardware to transmit, process, and store quantum information. QKD is safe from decryption by quantum computers. QNu Labs has successfully demonstrated the robustness of this technology.
In classical post quantum cryptography (CPQC), two parties use quantum methods, such as lattice-based encryption, to encrypt messages over classical channels (such as fibre-optic cable). This approach is safe from quantum-computing decryption. It requires hardware similar to what is required for traditional encryptions.
Post quantum cryptography is approaching. The right way to prepare for this new era varies by company, as do the considerations around balancing near-term costs with possible risks further in the future. Leaders and decision-makers in security and risk should evaluate their options and get moving.